Applying security policies to agents
You must apply at least one security policy to every agent group. Several secondary policies can also be added, and will apply when certain conditions are met.
EXAMPLE
You can add a conditional policy for mobile users, which applies when some workstations are no longer located within the internal corporate network. You could also define a quarantine policy that applies as soon as an agent's health indicators reach unsatisfactory levels.
To apply one or several security policies to an agent group:
- Go to the Policies tab in an agent group.
- In the Policies drop-down list, select the main security policy to be applied to all the agents in the group.
TIP
A blank policy is offered in the drop-down list. When one is used, the protection of an agent group (except self-protection) can be temporarily disabled, for example for tests and troubleshooting. - If necessary, click on Add a conditional policy. For more information, refer to Adding a conditional policy.
- By default, the Switch policies to detection mode option is enabled: the policy rules do not apply a block but generate a log. Disable this option to switch the policies to Protection mode.
-
In the window of the new conditional policy, select the policy which will be applied under certain conditions in the Policy drop-down list.
-
Click on Add a condition and give the condition a name.
-
Click on Add a test and choose from one of the following tests:
 IP address
IP addressEnter an IP address, address range or subnet and choose whether it needs to be within range or out of range for the test to be validated.
You can define several ranges separated by commas, For example 172.16.16.0/24,10.10.0.0/16.
 Reachable agent handler
Reachable agent handlerEnable this option to indicate that the agent must be able to reach the agent handler for the test to be validated.
 Ping
PingIndicate the IP address or network name of the host that you want to reach using pings, whether the agent must be able to reach it for the test to be validated, number of tries, and frequency of tries.
 Result of custom script
Result of custom scriptClick on
 to add a script, and specify its path, arguments and where to run it. Indicate what its Result must be for the test to be validated. This result must correspond to an output code of the script.
to add a script, and specify its path, arguments and where to run it. Indicate what its Result must be for the test to be validated. This result must correspond to an output code of the script.
It is best to use Local service as this is an account with restricted privileges. Do not choose Interactive session or System accounts unless absolutely necessary.Do note that even if you have prevented scripts from being run in your security policies, SES Evolution will assume that your internal custom scripts are trustworthy and allow them to be executed.
 Login to a domain
Login to a domainEnter the name of the domain and indicate whether the agent needs to be connected for the test to be validated. A value of Not connected indicates that:
- The agent is not linked to the domain in question,
- If the agent is linked to the domain, that it is not connected to the domain network.
 Status of a network interface
Status of a network interfaceClick on
 to add a network interface, and specify its name, unique ID (GUID) or description. Indicate as well what its status must be for the test to be validated: Connected or Offline or idle.
to add a network interface, and specify its name, unique ID (GUID) or description. Indicate as well what its status must be for the test to be validated: Connected or Offline or idle.
The Name and Description of an interface can be seen in the Windows Network & Internet panel.
Under Windows 10, to obtain all the information concerning an interface, including its GUID, run the following PowerShell command:
Get-NetAdapter | Select Name, InterfaceName, InterfaceGUID, InterfaceDescription, Status -
Add other tests if necessary, and click on OK. The sequence of the tests does not matter because ALL tests must be validated before the condition can be met.
-
Add other conditions if necessary. As soon as one condition is met, the corresponding policy will apply.
Conditions apply in the order of their appearance. -
If you want to run a custom script every time the conditional policy is applied, click on Add a task. When the script is added, specify its path, arguments and where to run it.
It is best to use Local service as this is an account with restricted privileges. Do not choose Interactive session or System accounts unless absolutely necessary. -
Under Triggers, select one or several events that will trigger the verification of conditions:
- Enable Every to check conditions at the regular interval that you specify.
- Enable Network event to check conditions if the workstation network interface changes, e.g., if it is connected to a Wi-Fi network, if it is a laptop plugged into a docking station, etc.
-
Click on OK. A summary of the conditions will appear in the Policies tab of the agent group.
-
Arrange the conditions in the sequence of your choice using the arrows on the left. The sequence of conditional policies is important.
EXAMPLE 1
Quarantining a workstation if its health indicators are unsatisfactory.
In this example, every 10 minutes, a script will run on the agents and check their health status. If an agent's results are unsatisfactory, the Quarantine policy will be applied to the agent and a second repair script will run. A quarantine policy isolates an agent by blocking, for example, its communications over the network and all removable devices, except those used by administrators.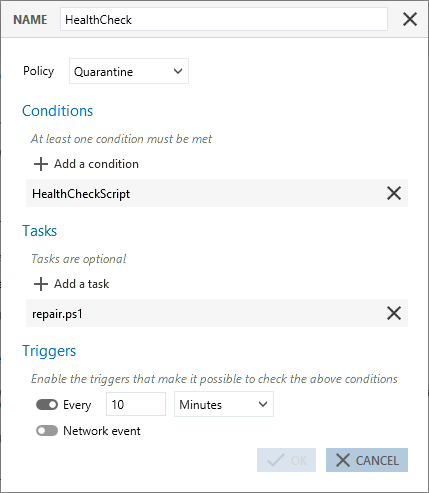
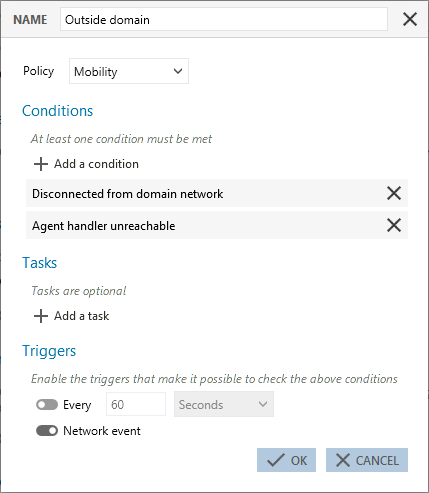
Applying a specific policy for laptop computers.
In this example, every time a network event occurs on a workstation, SES Evolution will launch all the tests defined for this condition:
- The workstation is not connected to its domain network,
- The agent handler cannot be reached.
If the results of the tests are positive, the Mobility policy will be applied.