Main principles for internal users
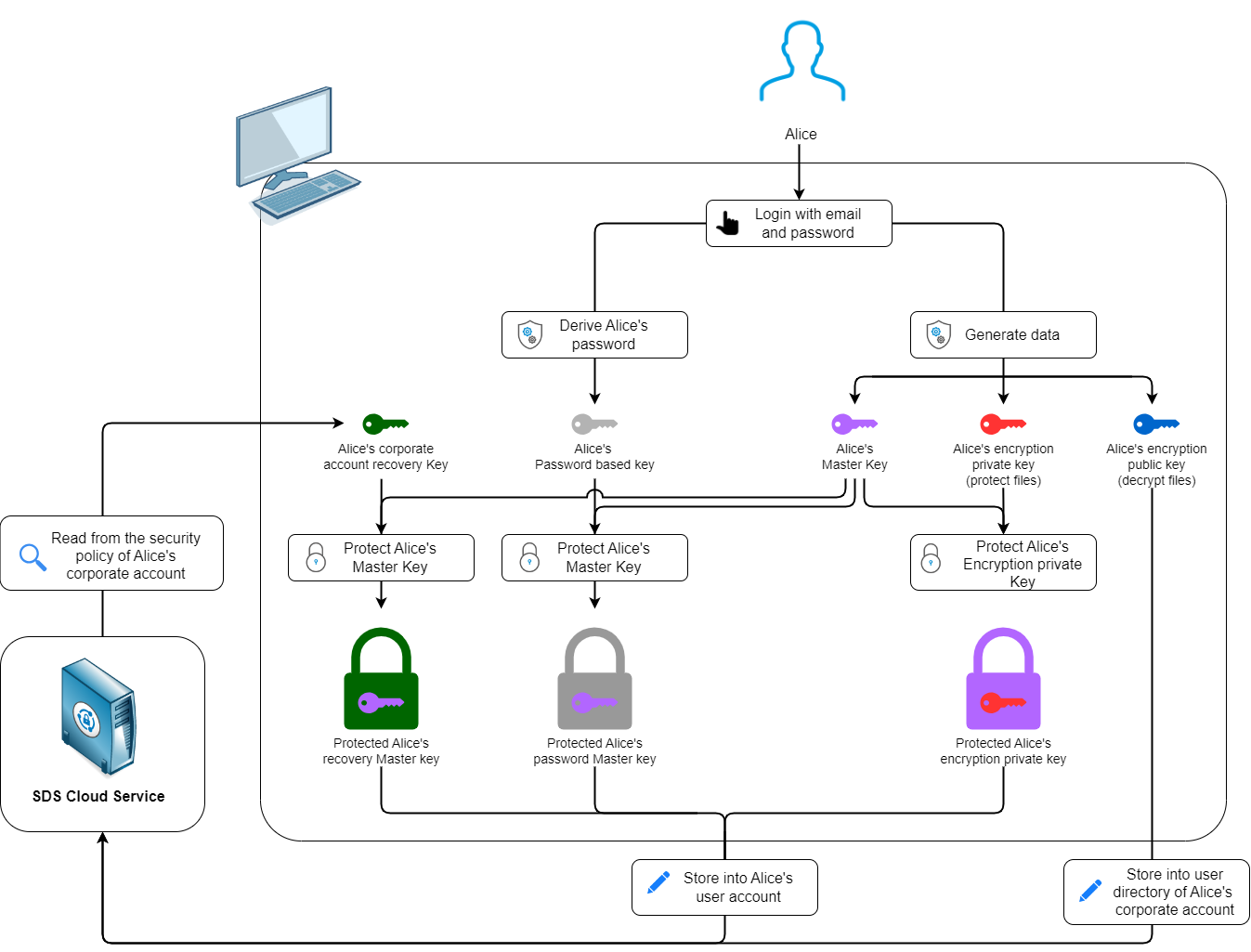
When a user creates an account in built-in key management mode, SDS Encryption Portal generates the following keys:
- The user’s master key (purple key in the diagram),
- The user’s private key (red key in the diagram),
- The user’s public key (blue key in the diagram),
- The password key derived from a password hash (gray key in the diagram).
An SDS Encryption Portal user (Alice in the diagram) has a public key stored in the SDS cloud service, which all users of the corporate account can access. The public key makes it possible for these users to protect files for Alice. This is the only key saved in plaintext because it does not contain any sensitive information and is therefore not confidential.
Alice needs her private key to read files that were protected for her. This key is wrapped with an intermediate asymmetric key, which is itself wrapped with the master key. As for the master key, it is wrapped in two ways:
- With Alice’s password key, which only she knows (gray padlock in the diagram),
- With the public recovery key (green key in the diagram). The private recovery key is stored in the account of the recovery user and is protected with this account’s master key, which is itself protected with a password.
As a result, Stormshield can never read your data, and no sensitive information is stored in the SDS cloud service.
The password key is derived from the user's password and never leaves the user’s device. It is used to wrap the master key of the user’s account. This master key will then be sent to the SDS cloud service database; the password itself is never stored. With this double level of protection, potential attacks are minimized.
The user’s password key is the starting point in the process of decrypting a file – with it, the master key can be located, which itself makes it possible to locate the private keys needed to decrypt data.
SDS Encryption Portal never uses the password itself, only derivatives, i.e., the password key and/or this same key wrapped with the master key.
The password makes it possible to:
-
Locate the master key to access sensitive data in the user account,
-
Authenticate the user on SDS Encryption Portal.
The user’s keystore, which will be used to decrypt files, contains confidential data. It consists of the following keys:
-
The master key wrapped in the password key,
-
The master key wrapped in the public recovery key,
-
The private key wrapped in an intermediate asymmetric key, which is itself wrapped in the master key.