Configuring the identity provider
The SDS encryption service for Google Workspace uses an identity provider (IdP) to authenticate end users, manage their access and life cycle. It is compatible with Google Identity and third party identity providers based on the OpenID protocol.
The following procedure describes the configuration with Google Identity. For more information, refer to the Google documentation.
When using a third party IdP, get the client ID from the SDS encryption service for Google Workspace. Refer to the documentation of your IdP.
To provide your external guest users with access to your encrypted content, you must create a specific IdP to authenticate them. For more information, refer to the Google documentation on configuring a guest IdP for al external users.
-
Log into the Google Cloud Platform using an administrator account.
-
Create a new project by specifying a project name and the organization it is connected to.
-
In the APIs and services > Credentials pane, click Create credentials > OAuth client ID to create a credential for the new application to be used with the SDS encryption service for Google Workspace.
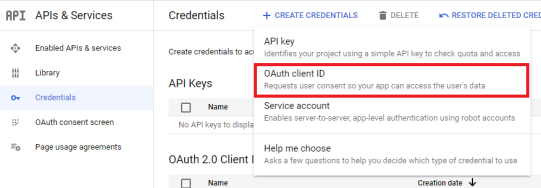
-
Click Configure the consent screen, then choose the Internal User type.
-
Click on Create.
-
In the Edit app registration pane, enter the parameters, then click on Save and continue.
You do not need to configure the scopes or the Google API library, as you only wish to get a credential to configure the IdP section on the Google administration console. -
Click Create credentials > OAuth client ID again, and in the Application type field, choose Web application.
-
Enter a Name, for example the name of the project.
-
In the Authorized Javascript origins area, enter the HTTP origins hosting your application:
-
https://admin.google.com
-
https://client-side-encryption.google.com
-
-
In the Authorized redirect URIs area, enter the paths the users are redirected to after Google authentication:
-
https://client-side-encryption.google.com/callback
-
https://client-side-encryption.google.com/oidc/cse/callback
-
https://client-side-encryption.google.com/oidc/drive/callback
-
https://client-side-encryption.google.com/oidc/gmail/callback
-
https://client-side-encryption.google.com/oidc/meet/callback
-
https://client-side-encryption.google.com/oidc/calendar/callback
-
https://client-side-encryption.google.com/oidc/docs/callback
https://client-side-encryption.google.com/oidc/sheets/callback
-
https://client-side-encryption.google.com/oidc/slides/callback
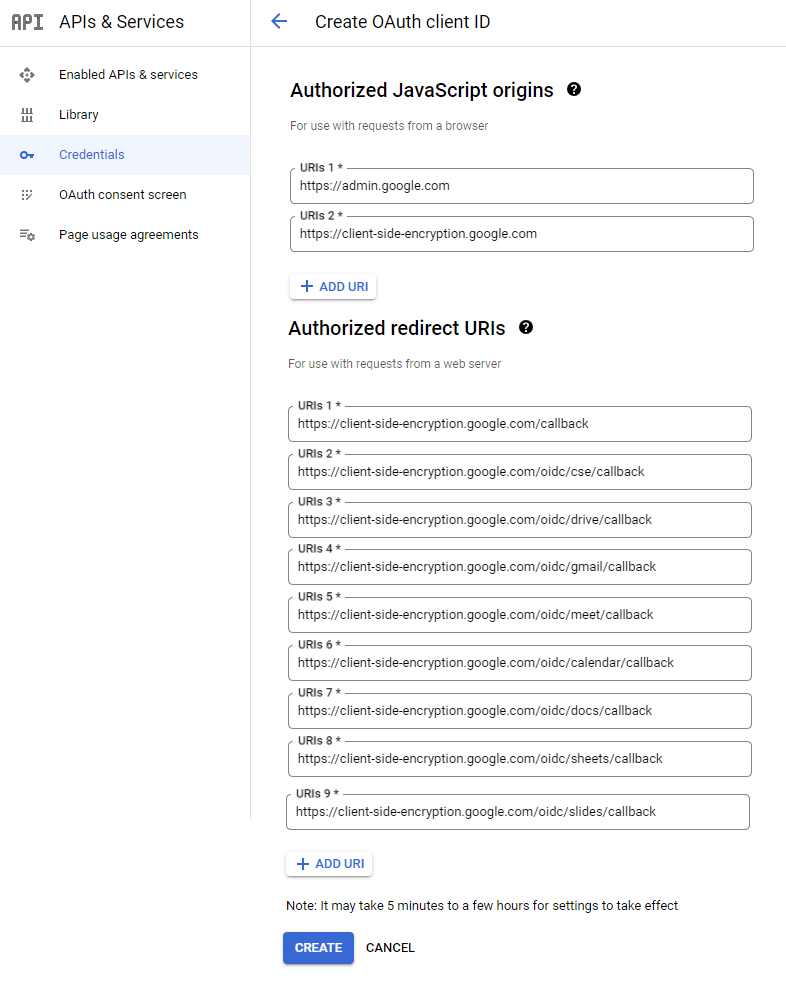
-
-
Click on Create.
The OAuth client is created. You can get its ID and download the corresponding JSON.
For Drive, Calendar and Meet mobile applications, as well as Google Drive for desktop, the Client IDs are as follows:
-
Drive for desktop:
947318989803-k88lapdik9bledfml8rr69ic6d3rdv57.apps.googleusercontent.com, -
Drive on Android:
313892590415-6lbccuf47cou4q45vanraqp3fv5jt9do.apps.googleusercontent.com, -
Drive on iOS:
313892590415-d3h1l7kl4htab916r6jevqdtu8bfmh9m.apps.googleusercontent.com, -
Calendar on Android:
313892590415-q84luo8fon5pn5vl8a6rppo1qvcd3qvn.apps.googleusercontent.com, -
Calendar on iOS:
313892590415-283b3nilr8561tedgu1n4dcm9hd6g3hr.apps.googleusercontent.com, -
Meet on Android:
313892590415-i06v47su4k03ns7ot38akv7s9ari5oa5.apps.googleusercontent.com, -
Meet on iOS:
313892590415-32ha2bvs0tr1b12s089i33o58hjvqt55.apps.googleusercontent.com.